Ubuntu desktop and server editions come with unattended-upgrades, which regularly check for outdated system packages and update them at specified intervals to protect the system against vulnerabilities and ensure it has the latest features and security patches.
This feature won't bother system administrators, but I've frequently heard Ubuntu desktop users complain that unattended-upgrades prevent them from immediately installing a package when they turn on their system.
So, today in this article, I'll show you how to disable the automatic update (basically "unattended-upgrades") feature on Ubuntu 24.04, 23.04, and other versions.
How to Disable Automatic Updates on Ubuntu 24.04
The first step (before stopping the automatic updates) is to check if the unattended-upgrades service is running on Ubuntu using the command below.
$ sudo systemctl status unattended-upgrades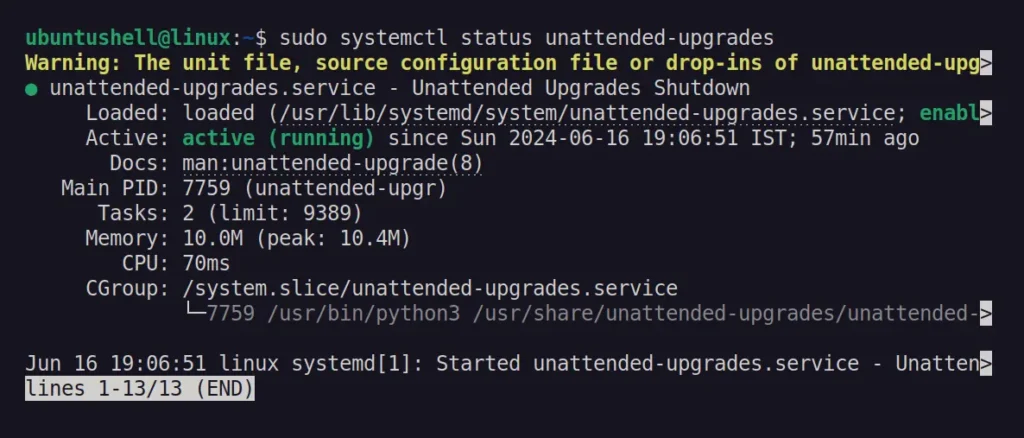
As you can see, it's active and running in my case, so if it's the same for you, you can follow any one of the mentioned methods to disable automatic updates on Ubuntu.
Method 1: Disable Automatic Updates on Ubuntu Graphically
The easiest way to disable automatic updates on Ubuntu is by opening "Software & Updates" using either the software-properties-gtk command or by launching it from the application menu.
Next, go to the "Updates" tab and choose "Never" for the "Automatically check for updates" setting.
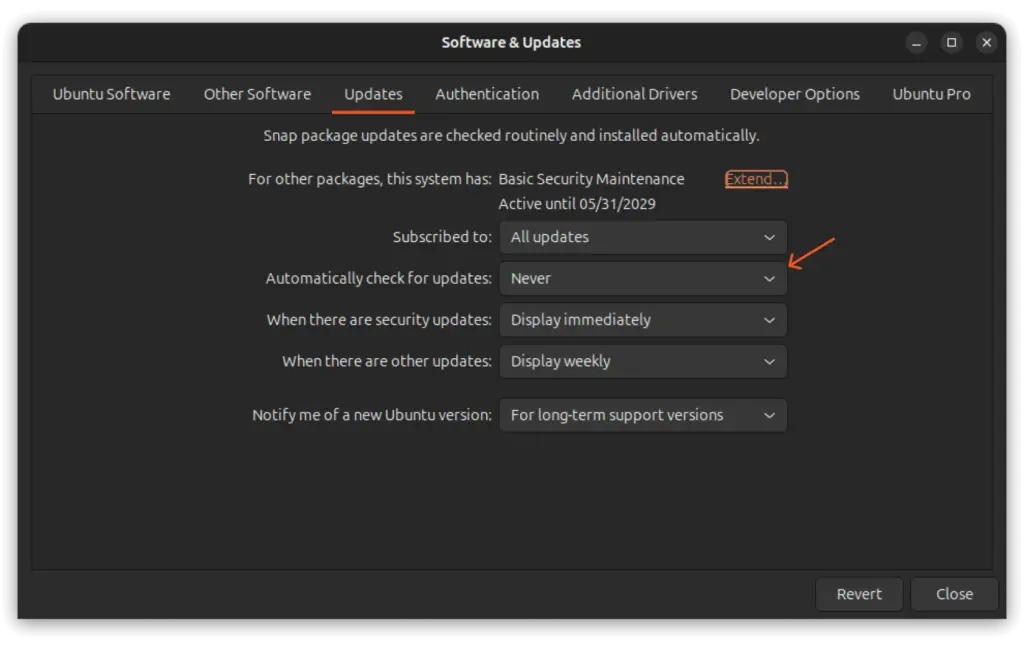
Similary, you can also change the "When there are security updates" from "Download and install automatically" to "Display immediately". This will notify you about any security updates as soon as they are available.
Method 2: Disable the Unattended-Upgrades Service
If you prefer the command-line for your daily work, you can stop and disable the unattended-upgrades service (responsible for automatic updates) using this command:
$ sudo systemctl disable --now unattended-upgrades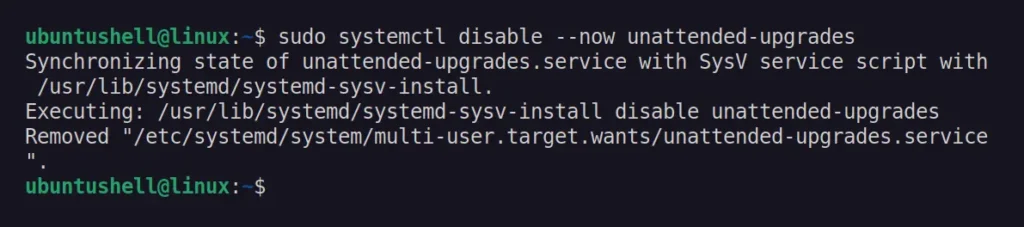
This will immediately stop the unattended-upgrades service, preventing it from starting automatically during system boot. If you ever want to start and re-enable the unattended-upgrades service, you can run sudo systemctl enable --now unattended-upgrades command.
Method 3: Edit the 20auto-upgrades Configuration File
📝 Note
It's not advised to follow this method, as users often forget that they have disabled automatic updates using the configuration file and find it hard to remember.
Another method to prevent Ubuntu from auto-updating involves editing the "20auto-upgrades" (or unattended-upgrades) configuration file. You can edit this file with Nano Editor using the command below:
$ sudo nano /etc/apt/apt.conf.d/20auto-upgradesWhen the file opens, change the values for the following attributes from "1" (yes) to "0" (no).
APT::Periodic::Update-Package-Lists "0";
APT::Periodic::Unattended-Upgrade "0";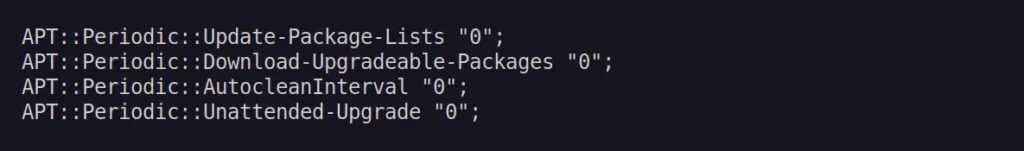
Once done, save and close the file.
These configuration changes would prevent unattended-upgrades from automatically downloading and installing updates. To re-verify whether automatic updates are disabled, you can run.
$ apt-config dump APT::Periodic::Update-Package-Lists
$ apt-config dump APT::Periodic::Unattended-Upgrade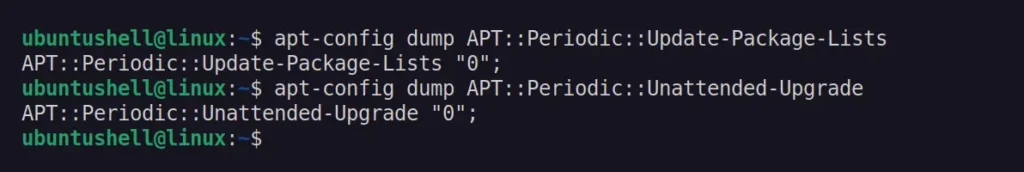
To re-enable automatic updates, simply edit the same configuration file and change the respective attribute values from "0" to "1".
Method 4: Uninstall the Unattended-Upgrades Package
To eliminate the root cause of your stress, you can permanently disable automatic updates by removing the unattended-upgrades package from Ubuntu using this command.
$ sudo apt remove unattended-upgrades -y
To reinstall it, you can use the sudo apt remove unattended-upgrades command.
How to Install Updates Manually on Ubuntu
To manually check for and install updates on your system, run the following update and upgrade commands:
$ sudo apt update
$ sudo apt upgradeIf you want to individually update a specific package, you can use the sudo apt upgrade <package-name> command.
While it's not recommended to disable automatic updates, especially on server systems, as they are always targeted by black-hat hackers. While desktop (or home) users can consider it unless they are connected to public Wi-Fi.
All the methods mentioned in this article work for Ubuntu and can also be applied to other systems such as Debian, Linux Mint, Pop!_OS, or any others that use the unattended-upgrades service for automatic updates.