Regular users are restricted from many activities to prevent accidental events or unauthorized access to system files.
In Linux, the only root user has permission to execute system-level commands. A standard user created using the adduser or useradd command is not granted those root-level privileges.
There is an indirect way to grant these privileges to the regular user by adding them to the sudo group. After that, we can attach the sudo keyword at the beginning of any commands to get root-level access.
Generally, it is recommended that every Linux user create an alternative user account with sudo privileges and operate with that account instead of directly operating the root account for daily work.
Today, you are about to learn how to create users, add them to the sudo group, and remove them in the future.
Creating a test User
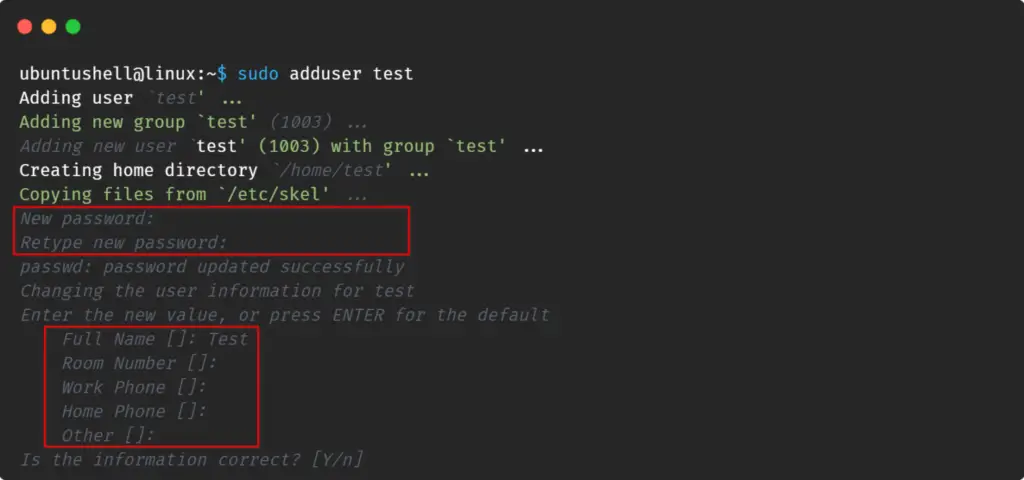
To demonstrate how to add a user to a sudo group, I will add a new user with the name "test" using the adduser command.
🔗 Listing All Users in a Linux System
The adduser command creates a new user with the user home directory and sets other important things.
- sudo adduser test
Replace the "test" username with yours while working. Once the above command is executed, it will ask for the user account password, name, and a few other details, as shown below.
Everything except passwords is optional, so they can be skipped. So now we are ready to add the "test" user to the sudo group.
Granting Sudo Privileges using the Usermod Command
In Ubuntu and all other Linux distributions, there is a usermod command that can help us add a regular user to the sudo group.
🔗 Execute Specific Commands Without Sudo Passwords in Linux
In the usermod command, we have to attach two options: the first is the -a flag, which means append, and the second is the -G flag, which stands for the group. After that, we will specify a sudo group with a username, meaning to append a user to the sudo group as shown below.
📝 Note
Granting sudo privileges to regular users requires a root account or an existing account with sudo privileges.
- sudo usermod -aG sudo test
Replace the "test" user with your custom username to get sudo privileges. After that, you can verify if that user was added to the sudo group or not using the below command.
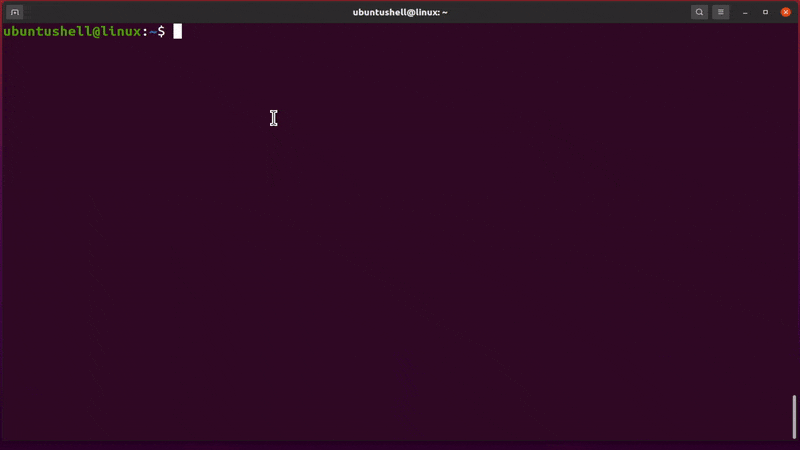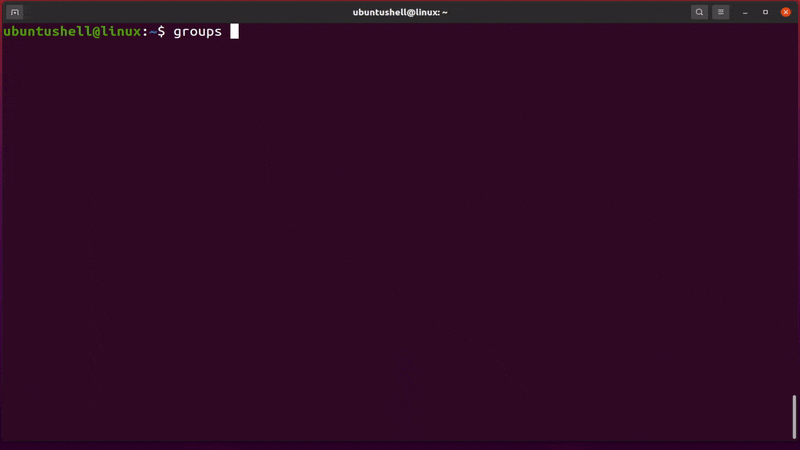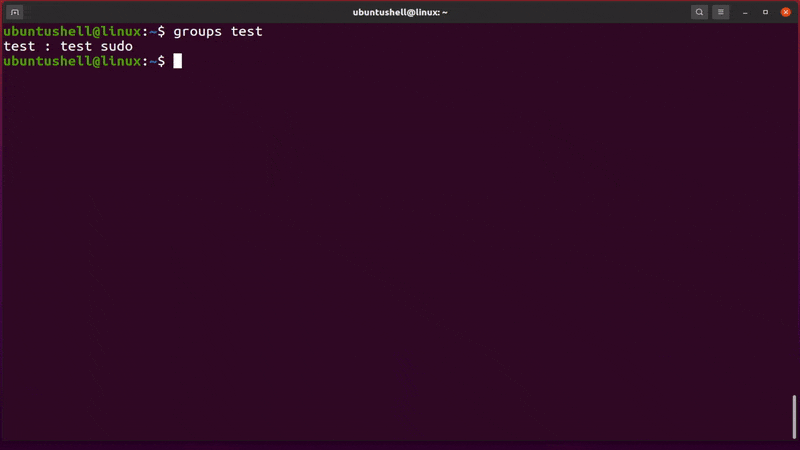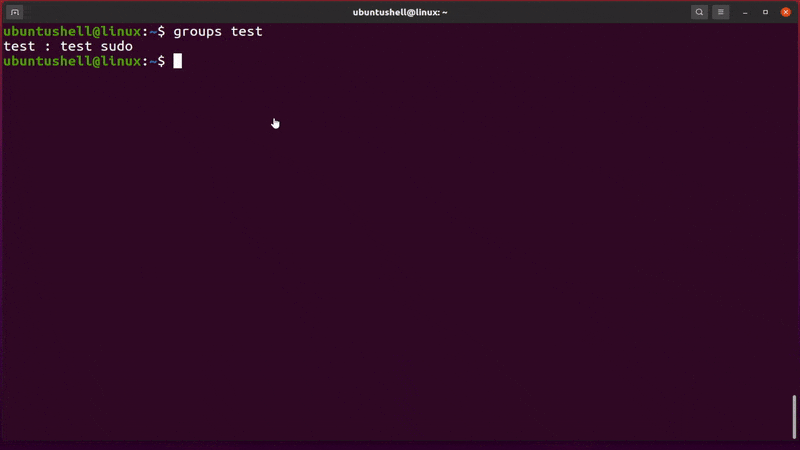
- groups test
Below is the behavior of the above command.
At the end of the line, the sudo keyword has been added, meaning the user has been successfully added to the sudo group.
After adding the user to the sudo group, you can execute any command with sudo privileges by adding sudo in front of the command, as shown below.
- sudo apt update
When executing the command with sudo, it will require a user account password. In my case, it will be a “test” user password that we set up while creating an account.
Remove Sudo Privileges from a User
Accidentally added different users to the sudo group or want to remove an already existing user from the sudo group? Both can be done using the deluser command.
The deluser command helps us detach groups from users. You must specify the username in this command and then group to detach, as shown below.
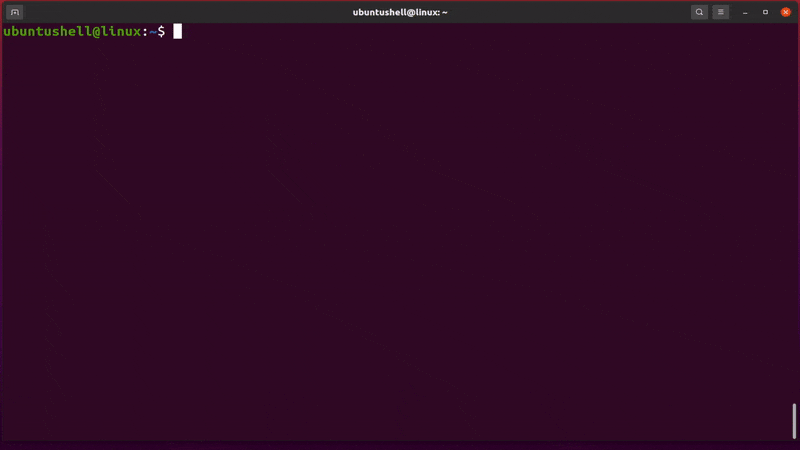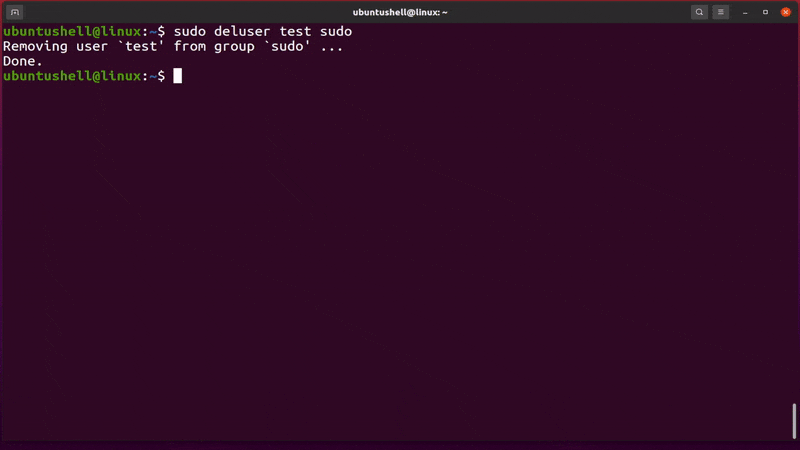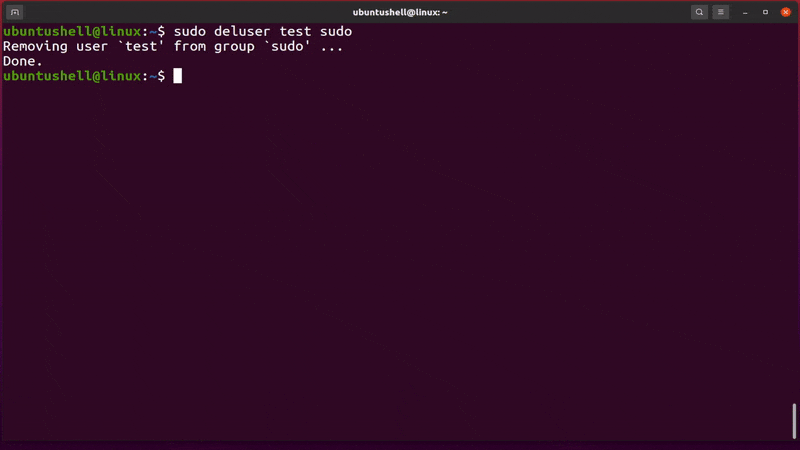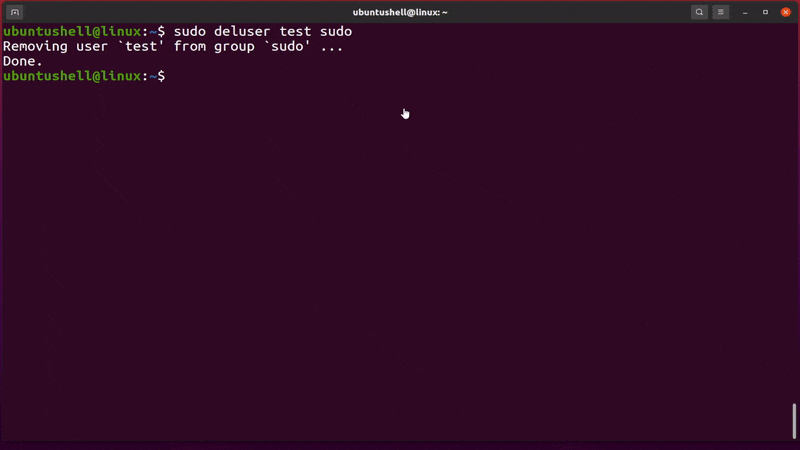
- sudo deluser test sudo
The above command removes the "test" user from the sudo group, as shown below.
Wrap Up
Many Linux users believe that sudo is safer than root because it requests a password on command execution.
Initially, the attempt to create sudo was to give users access to execute certain commands without giving them a root password.
This maintains the level of dignity between root users and regular users and maintains the system's security.